Blog
How can organizations prevent identity theft?
Friday, 09 April 2021
Identity theft is most often associated with the act of stealing an individual’s identity. Businesses have all the sorts of personal data like taxation and bank account details that individuals have, which can be stolen and abused. These are not just security breaches or employees misusing corporate assets here but also an identity thief pretending
- Published in Uncategorized
Secure login with FIDO2 explained
Sunday, 04 April 2021
Logging onto a website using your user name and password is no longer the best certification method for various reasons. On the one hand, entering personal user information is becoming increasingly cumbersome due to the ever-increasing number of services an average person uses. On the other hand, the security of log-in data is increasingly at
- Published in Uncategorized
What is fingerprint authentication?
Monday, 29 March 2021
Everyone has patterns of friction ridges on their fingers, and it is this pattern that is called the fingerprint. Fingerprints are uniquely detailed, durable over an individual’s lifetime, and difficult to alter. Because there are countless combinations, fingerprints have become an ideal means of identification. A fingerprint scanner is a type of technology that identifies
- Published in Uncategorized
iAmarsingh explains how to secure a YouTube channel
Thursday, 18 March 2021
iAmarsingh explains how to secure a YouTube channel from hacking.
- Published in Uncategorized
Sharmaji Brothers Explain How To Protect YouTube, Facebook, Twitter Accounts From Hacking
Thursday, 18 March 2021
Sharmaji Brothers explain how you will be able to secure your YouTube, Twitter and Facebook account by adding Security Key on your account. So if you want to know how to add Security Key in Google account. watch this video till the end.
- Published in Uncategorized
What is NFC and its use in security tokens?
Thursday, 11 March 2021
NFC stands for Near Field Communication and it enables short-range communication between compatible devices. It is a set of communication protocols for communication between two electronic devices over a close distance. NFC offers a low-speed connection with simple setup that can be used to bootstrap more-capable wireless connections. NFC works on the principle of sending
- Published in Uncategorized
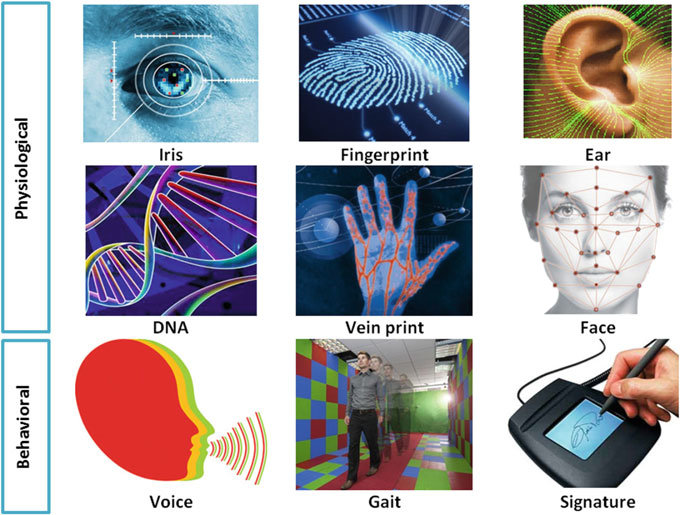
What is biometric security?
Monday, 01 March 2021
Biometric security is a security mechanism used to authenticate and provide access to a facility or system based on the automatic and instant verification of an individual’s physical characteristics. It involves using biometric security software to automatically recognise people based on their behavioural or biological characteristics. The biometric technology currently used most often in physical
- Published in Uncategorized
How to protect your login credentials from getting stolen?
Tuesday, 23 February 2021
Authentication software or security codes downloaded on a computer or phone are vulnerable to modern phishing and Man-in-the-Middle (MITM) attacks. And re-typing a code from one device to another wastes time and is prone to error. Use Security Tokens or Keys Thousands of companies and millions of end-users use security keys to simplify and secure
- Published in Uncategorized
What is Phishing?
Sunday, 21 February 2021
Phishing is the fraudulent attempt to obtain sensitive information or data, such as usernames, passwords and credit card details or other sensitive details, by impersonating oneself as a trustworthy entity in a digital communication. Typically carried out by email spoofing, instant messaging, and text messaging, phishing often directs users to enter personal information at a
- Published in Uncategorized
Why Should Companies Go Passwordless?
Wednesday, 17 February 2021
Passwords are a thing of the past In the earlier days of computing, you could trust people and their passwords because access was defined by physical perimeters. As IT has evolved, so have identity attacks making passwords the weak link in your organization. Passwords are costly for IT to support Passwords create a significant amount
- Published in Uncategorized
Competition Boss explains the concept of Security Key
Monday, 15 February 2021
Competition Boss explains the concept of Security Key and how it’s useful for digital protection against identity theft.
- Published in Uncategorized
How MrGamerJay’s YouTube channel got hacked
Monday, 15 February 2021
MrGamerJay explains how his YouTube account had got hacked and what he recommends for ultimate hack-proof protection.
- Published in Uncategorized
Malvika Uses Movie Story to Highlight Online Identity Theft
Saturday, 13 February 2021
In this video, Malvika discusses an awesome new Netflix series, Lupin. Assane Diop is a charismatic thief with a troubled past. Watch his journey and learn about Arsène Lupin in the process. Definitely check out the cool short film written and directed by Malvika introducing the Legend of Arsène Lupin. Diop is a con man
- Published in Uncategorized
What Is a Security Key or a Token?
Friday, 12 February 2021
A security key (also know as a security token) is a portable device that authenticates a person’s identity electronically by storing some kind of personal information. The owner plugs the security token into a system to grant access to a network service. Security tokens come in many different forms, including hardware tokens that contain chips,
- Published in Uncategorized
Security Key for 2 factor authentication | How to use Yubikey 5 NFC
Wednesday, 20 January 2021
In this video Nabeel Nawab shows you how a hardware security key which is used for two factor authentication, save YouTube account from being hacked. The key he uses is a Yubikey 5 NFC.
- Published in Uncategorized