We're one-stop shop for security keys and security tokens. With a solid track record, we're also preferred partners of several global OEMs.
Buy security
keys and
security tokens
© TheSecurityKey.com
All Rights Reserved
Powered by WebbleGum

Logging onto a website using your user name and password is no longer the best certification method for various reasons. On the one hand, entering personal user information is becoming increasingly cumbersome due to the ever-increasing number of services an average person uses. On the other hand, the security of log-in data is increasingly at risk due to cybercriminals becoming sneakier and more technologically advanced. Targeted brute force attacks or seemingly harmless email phishing attacks accumulate so users often don’t even notice that their own login data has already been tapped.
The FIDO2 security standard addresses this problem by enlisting the help of two-factor authentication that uses security keys (FIDO2 keys) and hardware tokens. Thanks to the integration of the W3C standard WebAuthn, this procedure not only allows encrypted and anonymous logins, but also completely passwordless logins.
FIDO2 is an open authentication standard, hosted by the FIDO Alliance, that consists of the W3C Web Authentication specification (WebAuthn API), and the Client to Authentication Protocol (CTAP). CTAP is an application layer protocol used for communication between a client (browser) or a platform (operating system) with an external authenticator such as security keys.
FIDO2 is an extension of FIDO U2F, and offers the same level of high-security based on public key cryptography. FIDO2 offers expanded authentication options including strong single factor (passwordless), strong two factor, and multi-factor authentication. With these new capabilities, many security tokens can entirely replace weak static username/password credentials with strong hardware-backed public/private-key credentials. These credentials cannot be reused, replayed, or shared across services, and are not subject to phishing and MiTM attacks or server breaches.
Use of a hardware-based security key is fast and easy. For FIDO2 supported services, users are freed from having to remember and type passwords.
Replaces weak passwords with strong hardware-based authentication using Private / Public Key (asymmetric) cryptography.
A single security key that can work across thousands of accounts with no shared secrets.
Strong single factor authentication using a hardware authenticator, eliminates the need for weak password-based authentication.
Strong two factor authentication using a hardware authenticator as an extra layer of protection beyond a password.
Strong multi-factor authentication using a hardware authenticator and a PIN or biometric, to meet high assurance requirements such as needed for financial transactions and ordering a prescription.
The main goal of FIDO Alliance is to increasingly eliminate passwords on the web. In order to achieve this, the secure communication path between the client (browser) and the respective web services is first set up or registered in order to be permanently available for later logins. In this process, FIDO2 keys are generated and verified, which provide the basic encryption for the logon procedure. The procedure is as follows:
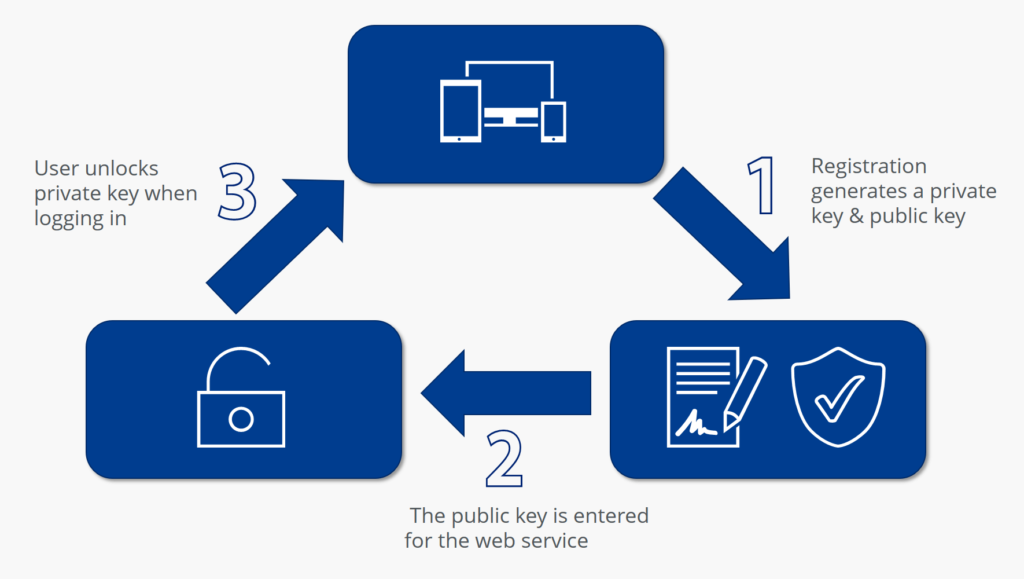
Yes, FIDO2 security tokens/keys are available here: https://thesecuritykey.com/supported-protocols/fido2
We're one-stop shop for security keys and security tokens. With a solid track record, we're also preferred partners of several global OEMs.
© TheSecurityKey.com
All Rights Reserved
Powered by WebbleGum

You must be logged in to post a comment.